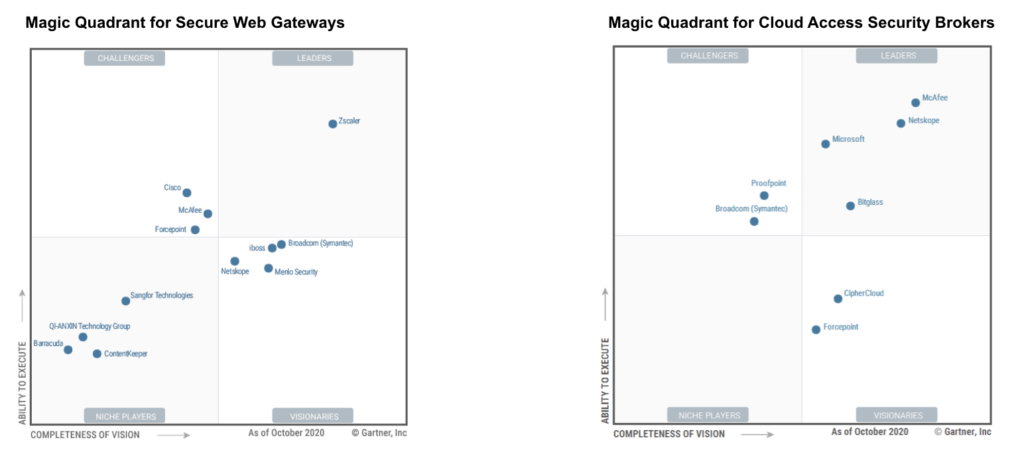
Gartner’s recently released 2020 versions of the Magic Quadrant for Cloud Access Security Brokers (CASB) and the Magic Quadrant for Secure Web Gateways (SWG) tell us a lot about where both markets are headed. Data and users increasingly reside and work in the cloud, the global pandemic has accelerated digital transformation in unprecedented ways, and the march is on toward the Secure Access Service Edge (SASE) future Gartner first predicted in its 2019 paper, “The Future of Network Security Is In the Cloud.” As the status quo of security inverts from the data center to the user, CASB and SWG increasingly will be the same conversation, not separate technology markets.
In other words, will there even need to be separate CASB and SWG magic quadrants in the future? At Netskope, we don’t think so.
There are four key transformations at play, including networking, security, applications, and data. Each has an impact on the required capabilities for CASB and SWG in the context of SASE architecture.
- Networking transformation reduces backhauling, hairpinning, and latency to provide direct to cloud access between users and apps. Remote working is at an all-time high and is predicted to remain well above pre-pandemic levels for the foreseeable future. Users are embracing direct-to-cloud access as opposed to using VPNs and MPLS networking to backhaul to central office egress points for web and cloud services. The many positives for this transformation include a reduction in MPLS and VPN expenses, a simplified environment, and an improved user experience for web, SaaS, and cloud services.
- Security transformation reduces data center, office, and branch office security appliances, moving to a cloud secure access edge with a single pass inspection of user traffic for web, managed SaaS, unmanaged SaaS (Shadow IT), public cloud services, and custom apps in these cloud services. These five types of user traffic all require data and threat protection with granular policy controls by user, group, or OU, and by app, instance, activity, data, and other contextual variables. The givens for security transformation are TLS traffic inspection, Zero Trust Network Access (ZTNA) to data and resources, plus the ability to support any user, device, or location.
- Application transformation migrates apps from the data center to new SaaS replacement choices, new or redesigned custom apps architected for the cloud, or the lift and shift of legacy apps to cloud-hosted virtual machines. SaaS app adoption has nearly doubled year over year from an average of 1,295 apps per organization in 2019 to 2,415 in 2020 based on Netskope Research Labs. The key point for app transformation is less than 2% of these apps are managed by IT with administration rights. The rest are freely adopted by users and business units making Shadow IT a growing security risk.
- Data transformation migrates data out of the data center into apps and cloud services where most of the data resides, however, data exposure happens via boundary crossings into personal instances of managed apps, unmanaged apps (Shadow IT), or data shared via collaboration, social, and web activity. Organizational leaders managing data protection and risk often track this transformation in cloud risk assessments with a focus on Shadow IT and app profile risk ratings. The net result is driving new use cases to control unintentional or unapproved data movement, protection of data and IP from cloud and web-enabled threats, plus providing granular policy controls based on data context to apps and cloud services with data protection and advanced DLP.
None of these four transformations favors a singular focus on CASB or SWG.
The market has generally viewed CASB for managed apps and cloud services using an API deployment working out of band to analyze data-at-rest. Associated cloud security solutions also include API-based cloud security posture management (CSPM) and cloud workload protection platforms (CWPP) for managed cloud services. This makes sense for managed apps and cloud services controlled by IT, however, business units and user-led adoption of Shadow IT are a runaway train that needs to be addressed, alongside personal instances (vs. company instance) of managed apps users also access. A SASE architecture requires inline data context, shifting the emphasis for CASB solutions going forward.
Putting a singular focus on SWG emphasizes web threats via an inline proxy solution with advanced threat defenses including pre-execution analysis, sandboxing, machine learning analysis, and remote browser isolation. Given the internet has been the leading source of threats, this makes sense. However, threats are shifting towards SaaS; APWG.org Phishing Trends Report notes the number one phishing target is SaaS/webmail for two years running. SaaS is also being used to attack SaaS, where the leading example is cloud phishing using fake login forms hosted in trusted cloud storage apps. Even the 2020 Verizon Data Breach Investigations Report (DBIR) highlights the focus on credentials and access compromise for incidents and breaches–why break in when you can log in? A SASE architecture requires both cloud and web traffic in a single pass proxy architecture with associated defenses for data and threat protection.
Past security and networking leaders are facing new challenges for their existing solutions as the pandemic and increased remote working accelerate disruptive transformation. Consolidation, reduced complexity, and lower costs are benefits of change for the network and security transformations many vendors are quick to emphasize. However, application and data transformations are becoming more disruptive as they drive new use cases, seek to manage risks, and protect data and users. Solutions that address application and data transformations are best suited for the data context of a SASE architecture. In the very near future, the conversation will not be about who has the best CASB or the best SWG, or any other individual piece of a SASE architecture. To get to SASE, it’s time to focus on effective single-pass, integrated CASB and SWG solutions going forward.
Your SWG is blind to more than 50% of your traffic and we can Prove It. Experience the transformation today.




 Indietro
Indietro
















 Leggi il blog
Leggi il blog